PRE-GUIDED BLOG
(see GUIDED BLOG below for updates)
[This is a theoretical blog on how to setup HA-HB server]
What you need?
- 2 Connected computers
- Heartbeat (Daemon)
- Pacemaker (Cluster Resource Manager / CRM)
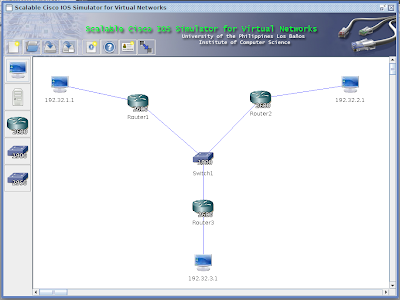
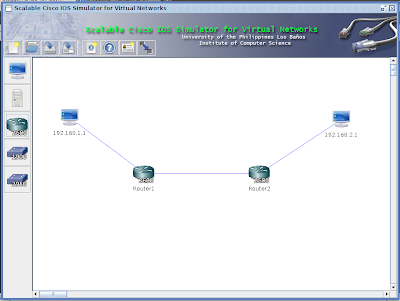
In the original discussion the setup is created using a switch ( connected to the internet ) 2 servers (computers) one will be the primary and the other one is the backup. This servers are connected directly via a ethernet crosscable and a serial cable ( in order to pass data ). Since we do not have a ethernet cross cable at our disposal. We will copy the setup that we did in our last exercise (DHCP configuration). Instead of using a ethernet cross cable we will connect them wirelessly.
After creating the topology we will now proceed into configuring the 3 core files in heartbeat these are:
- /etc/ha.d/ha.cf
http://www.linux-ha.org/doc/users-guide/_creating_an_initial_heartbeat_configuration.html#_the_literal_ha_cf_literal_fileautojoin none mcast bond0 239.0.0.43 694 1 0 bcast eth2 warntime 5 deadtime 15 initdead 60 keepalive 2 node alice node bob pacemaker respawn
- /etc/ha.d/authkeys
http://www.linux-ha.org/doc/users-guide/_the_literal_authkeys_literal_file.htmlauth <num> <num> <algorithm> <secret> or
( echo -ne "auth 1\n1 sha1 "; \ dd if=/dev/urandom bs=512 count=1 | openssl md5 ) \ > /etc/ha.d/authkeys chmod 0600 /etc/ha.d/authkeys
- /etc/ha.d/haresources
http://voices.yahoo.com/installing-configuring-heartbeat-ubuntu-server-3778384.html?cat=15
http://clusterlabs.org/doc/en-US/Pacemaker/1.1/html/Clusters_from_Scratch/
or
http://www.zivtech.com/blog/setting-ip-failover-heartbeat-and-pacemaker-ubuntu-lucid
After doing the steps in the link above hopefully we are done.
REFERENCES:
In this part I have failed to start the heartbeat because node2 is non existent that's why on the upper portion of the blog I have stated that we need 2 Computers because I have overlooked the fact that each node corresponds to a computer. This steps also failed to accomplish the pacemaker part thus I think this setup is incomplete.
- HEARTBEAT - http://www.linux-ha.org/doc/users-guide/users-guide.html
- PACEMAKER - http://clusterlabs.org/doc/en-US/Pacemaker/1.1/html/Clusters_from_Scratch/
- HEARTBEAT + PACEMAKER - http://www.zivtech.com/blog/setting-ip-failover-heartbeat-and-pacemaker-ubuntu-lucid
- http://voices.yahoo.com/installing-configuring-heartbeat-ubuntu-server-3778384.html?cat=15
[This part is what I did step by step in configuring the heartbeat only using : http://voices.yahoo.com/installing-configuring-heartbeat-ubuntu-server-3778384.html?cat=15]
 |
| Configuring /etc/ha.d/ha.cf |
 |
| Configuring /etc/ha.d/authkeys |
 |
| Configuring /etc/ha.d/haresources |
 |
| Starting Heartbeat |
GUIDED BLOG
After failing to configure heartbeat successfully during the first two sessions, we have now a guide on how to accomplish the task. Here is the list of tasks that are needed to be done in order to accomplish heartbeat.
Step 0: Remove/Purge Heartbeat and Apache2
Since other students have used the computer, their previous configurations are present so we need to do a sudo apt-get purge apache2 heartbeat or sudo apt-get remove --purge apache2 heartbeat in order to remove their configurations. (Note: we can eliminate redundant typing of sudo by typing first sudo -s).
 |
| Removing Previous Installations. |
Step 1: Changing host names
We need to change hostnames in order to identify computer1 from computer2 since all computer in the pclab are named user. To change the hostnames we need to do to steps.
- Type sudo hostname <your_hostname> // in our case it is server1
- Edit /etc/hostname and change the content of it to <your_hostname>
Step 2: Installing Heart Beat and Apache2
 |
| Installing Heartbeat and Apache on Server1 |
 |
| Installing on Server2 |
It seemed awkward to me because if the goal of the exercise is to fetch the data if server1 died out. Then why is it that the returned html file if server1 died out is not the html file of server1 instead it is the html file of server2. I think this can be answered by a principle in DBMS, maybe server1 and server2 are connected to a remote server thus serving same file. We only show different kind of html to demonstrate that server2 catches the requests if server1 dies out.
 |
| Modifying index.html |
Step 3: Configuring
- ha.cf
- haresources
- authkeys
After installing the needed tools, we will now proceed in configuring the setup of heartbeat.
1. ha.cf configuration
We configure ha.cf in vi. We can do this by typing vi /etc/ha.d/ha.cf, type the necessary lines of codes shown in the picture below on both server 1 and 2. The lines here configures the needed configurations in order for the heartbeat to run.
2. haresources
After configuring ha.cf we now configure haresources. This file tells us what the Virtual IP of the main server is and what server application it is using. In our case it is apache2. Do this for both server1 and 2
3. authkeys
We now edit authkeys (or authentication keys in longer terms). This file is needed in order to ensure that the one accessing the server1 w/c is the backup server is the legit backup server. This file contains an encrypted password(in our case it is sha1, another example is md5). After that we need to set the permissions to 600 by typing chmod 600. This will ensure us that it can only be edited by our server.
Step 4: Edit /etc/hosts
In our previous exercises we already have configured this file. This file contains table with a combination of IP and sitename of hosts. So we can route to them. We need to configure this in order for our server to establish connections.
Step 5: crm configure edit
After editing /etc/hosts we now proceed to editing our cluster resource manager. This crm is pre installed in heartbeat (I think?). The problem is whenever I tried to do this by typing crm configure edit it will return an error that it cannot be configured because line one of the XML file is not found. Me and my partner anaylzed the problem and have found out that even though the XML file is there in /etc/var/lib? (i forgot the whole path, but it is where the xml file is located) the XML file is there. This may have been caused that we need permissions( but remember I already typed sudo -s at the start, I even tried sudo crm configure edit but did it did not work). This is the part where I have reached in configuring the heartbeat setup. This is also the second last part of the exercise.
Step 6: Restarting apache2 and heartbeat
We need to restart heartbeat and apache2 in order to apply the changes we have made in the configuration. After this we should test if our setup works.
Questions:
1. What are the problems encountered?
One of the major problem encountered is that even if you purge the current configurations of heartbeat and apache. The configuration file is still present. So after you installed them again, the previous configurations still persists.
Another problem is that students forgot to clean up what they have done. It gives us a hard time to configure since initial or some configurations have been altered already and some can't be altered for some unknown reason and most of us in the lab cannot even successfully run the program even though we followed the step by step procedure.
2. What are your insights about HA-HB?
I think ha-hb concept is great, because a website needs to be up at all times. Like in the movie "The Social Network" Mark Zuckerberg states that facebook must not shutdown ever.That is how crucial website up time is and I think HA-HB is perfect for this task.
3. State your ideas about the possible application of HA-HB?
Aside from facebook that I have mentioned earlier I think a potential application of HA-HB is in online banking, computer registration systems ( ie. Systemone, CRS of UPD) or any site that performs transactions.
4. What can you say about the mode of discussion?
I think it is good for the students to let them fend for themselves. With the theory given, they will learn more efficient because they are learning at their own pace. Although it is good I think they still need the supervision from their respective lab instructors just in case they suffer some problems that is not fully related or is out of scope of the exercise.